Summary
Cryptographic signatures are now deeply embedded into every aspect of Holochain’s data flow. We’ve also mapped out a clever way to use existing tools to allow Holo web users to maintain control of their identity as if they were native Holochain users. We have a few breaking changes for developers to note, as well as more improvements to the debugging experience.
Note: Unless otherwise mentioned, all features and bug fixes are currently available in the `develop` branch, and will be included in the upcoming `0.0.5` release.
Highlights
- Holochain App/Platform Builders: Get Listed on our Website
- Keys and Signatures Implemented Throughout Holochain
- Breaking Change: New Names for DNA Bundles and Build Scripts
- Networking Implementation Changes for Firewall Traversal
- WASM Panic Logging: Improving the Debugging Experience
- Tooling Setup: ‘Missing Dependency’ Messages
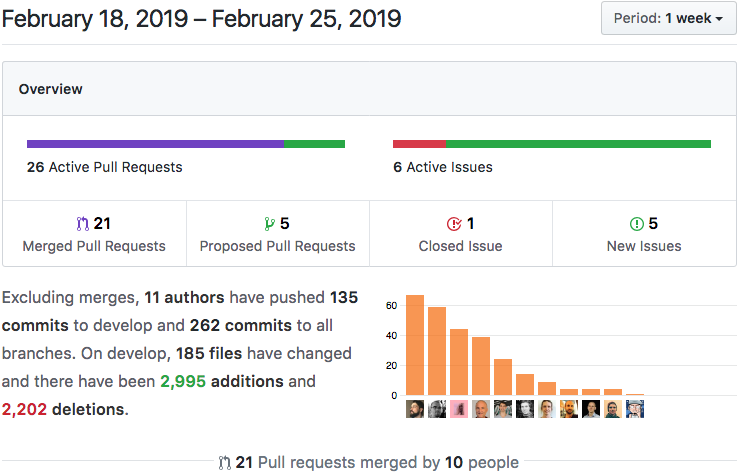
Details
1. Building an App/Platform on Holochain? We want to hear from you!
Are you building on Holochain? We would love to connect and hear more about your app/platform so please take a few moments to fill out this survey! We’re looking to list all the projects building on Holochain on our website.
2. Keys and Signatures Implemented Throughout Holochain
At its core, Holochain is a protocol and a development framework for building distributed apps that lets sovereign agents interact with one another safely.
Our resilience model rests on two key concepts, intrinsic data integrity and peer notaries. To support intrinsic data integrity, every piece of data is signed by its author.
This allows agents to verify the provenance of a piece of data and validators to produce proof if an agent has been acting in bad faith.
Signatures are now being produced and verified with real key pairs everywhere they should appear. This includes when data is committed to a source chain, is received by peers for validation and storage, or is retrieved from the DHT. (See an example of validating signed provenances.)
You can also use the `hc keygen` command to create passphrase-protected key pairs for your identity. On startup, the Conductor will look for the location of your key pairs in your configuration and ask you for your passphrase.
Breaking Change Warning: We’ll be changing the format of our encrypted keyfiles in the future; at some point you will have to regenerate your keys.
Errata: In the last Dev Pulse, we touched briefly on how we intend to give Holo web users full control over their identity. We mentioned that for the Closed Alpha we’d be implementing an interim feature that allows the hosting device to run the DNA, but also permits the web user to sign every entry. We mistakenly reported that the necessary hack was integrated into the Conductor; it turns out that all of the code has not yet been rolled into the `develop` branch. You can follow our progress here and here.
3. Breaking Change: New Names for DNA Bundles and Build Scripts
We want to introduce two breaking changes, both related to filenames. First, compiled DNA bundles will no longer be named `bundle.json`, and there will be no leftover `.hcpkg` file. Instead, bundles will have a nice name that follows the format `<app_name>.dna.json`. This file will be put into a `dist` directory by default.
Secondly, the build tool will now look for build scripts named `.hcbuild` rather than `.build` in the root of each zome folder — so make sure you rename all existing build scripts! We made these changes in order to be consistent with `.hcignore` and avoid collisions with other build tools.
4. Networking Implementation Changes for Firewall Traversal
One critical issue that plagues many P2P systems is punching through firewalls and routers — also known as NAT traversal. We had modest success with the IPFS project’s libp2p in the Go Prototype, but were never quite satisfied with its usability. The current networking prototype, which implements just enough to make Holochain functional, also used libp2p until recently. Our new native P2P gossip protocol now communicates over WebSocket. It doesn’t enable firewall traversal by itself, but it paves the way for a ‘Web Proxy’ solution which would allow native Holochain users and Holo hosting devices to advertise themselves as proxies for restricted devices.
5. WASM Panic Logging: Improving the Debugging Experience
Debugging is an area in which we want to make the developer experience better. You can output debugging messages from your DNA code, but the WASM boundary makes it hard to get details about the nature of the exception if you’re running DNA instance panics. We’ve improved the experience; the panic info will now be sent to the debug log. If you’ve compiled debug symbols into your DNA, it’ll also report the zome filename and line number. There are no call stack dumps yet, but we’re investigating something that might help it involves using headless browsers and wasm-bindgen when you’re running a DNA in dev mode.
6. ‘Tooling Setup: ‘Missing Dependency’ Messages
If you’re installing Holochain as a developer for the first time, there are a few dependencies you need to install first. You’ll now get friendly error messages if you try to run the `hc` development tool without those prerequisites.




