Anticapture? Capture-Resistance? Uncapturable?
We’ll get to these in a moment, but first: What is Capture?
“In politics, regulatory capture … is a form of corruption of authority that occurs when a political entity, policymaker, or regulator is co-opted to serve the commercial, ideological, or political interests of a minor constituency, such as a particular geographic area, industry, profession, or ideological group.”
— Wikipedia, Regulatory capture
More broadly we can think of capture as a type of control or corruption where a small group gains inordinate power over others and their interests. Whether that is capture of a resource, a process, or the flow of communication, a powerful minority takes control of the benefits of something that should be held in common.
Following we are going to look at a few different forms of capture and methods for avoiding it.
Anticapture
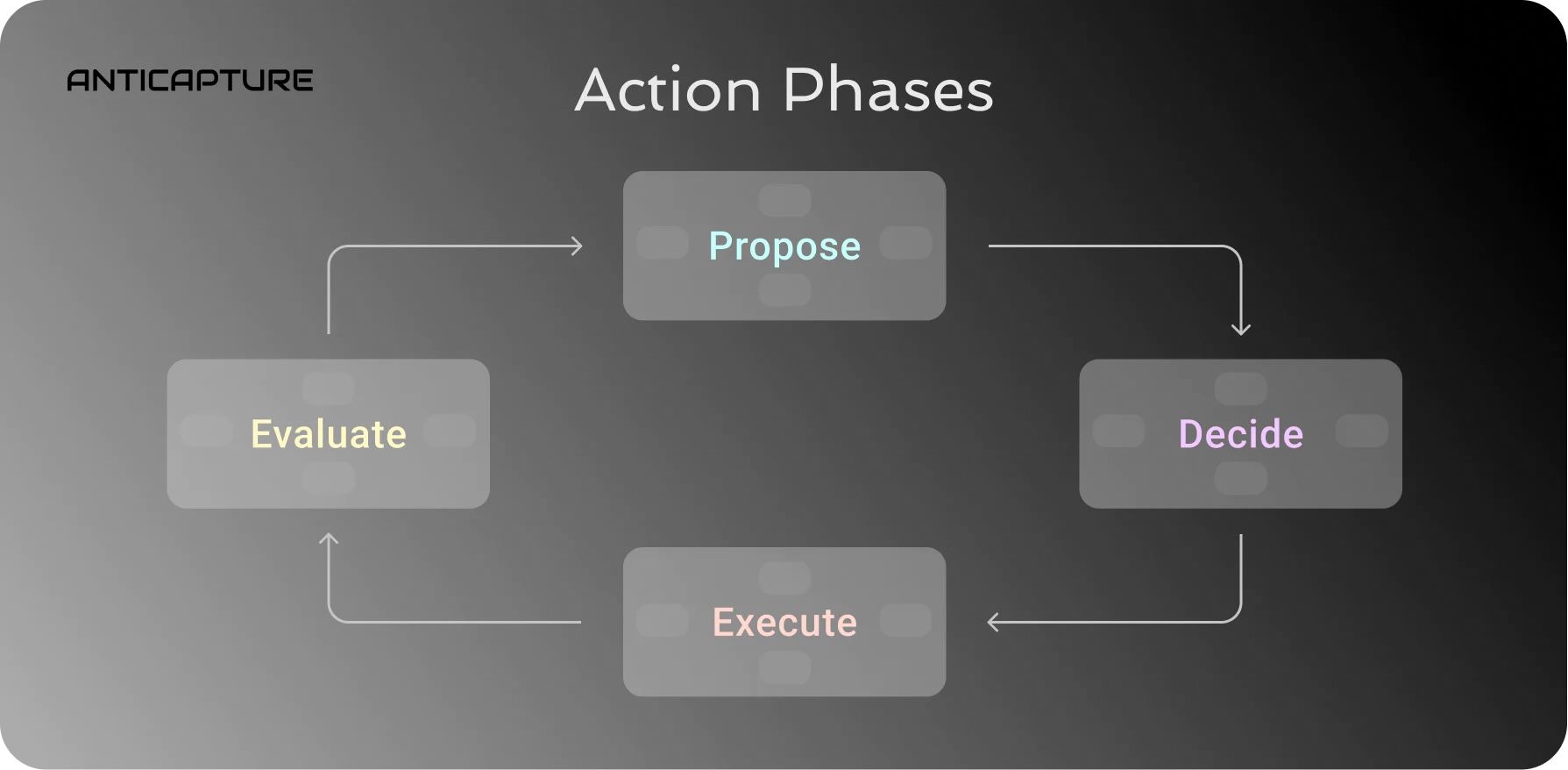
The Anticapture framework proposed by Spencer Graham outlines governance practices for managing shared resources collectively without a fraction of that collective capturing control of the resources. For this he proposes DAOs as an ideally capture-resistant structure, but in doing so he redefines a DAO as: “a network of agents who share common purpose, and are the only ones who hold the power to execute actions that manage a set of shared resources. The core of Graham’s work is focused on the key stages of governance which he outlines as follows.
Graham outlines governance practices for managing shared resources collectively without a fraction of that collective capturing control of the resources.
Anticapture describes four stages of decision making:
- Propose: delineate the options on the table
- Decide: select the preferred option
- Execute: put the selected option into action
- Evaluate: analyze the impact of the executed action
Of these, Graham sees the greatest security risk in the Execute stage. If the ability to execute action is captured then the resource is also captured. While he is not completely clear about the mechanics, he presents DAOs as addressing this by decentralizing action and giving the community the ability to act autonomously without outside influence (thus avoiding capture from regulators, for instance).
Assuming that the final execution of any action in a DAO is carried out by smart contracts, then the design of these contracts themselves and the infrastructures that they are built on are risk vectors for capture.
Capture Resistance Across the Web
Anticapture speaks to the level of the organization, but what of the infrastructures the organization is built on?
“For the longest time, word was that the Web would free the world; now, it seems as if most of the world wants to liberate the Web.” - Robin Berjon, Capture Resistance
The internet itself is a commons, a shared resource and infrastructure we all rely on, but due to its design we have seen many forms of capture overtake the internet, from data mining to market manipulation. Robin Berjon’s article Capture Resistance calls for new design standards to ensure that software and the underlying infrastructure of our web protocols do not allow for capture.
Berjon outlines four main attack vectors:
- Capability to observe the behavior of users on another business’s products:
Data mining, trackers, etc. - Defaults that project power laterally between markets:
Default search engines, browsers, and similar. - Intermediation which happens when an entity has power over relations between other entities:
Platforms that act as gatekeepers and extract rent from peer transactions. - Opaque mechanisms used in place of open markets:
Lack of clear rulesets that are mutually consented to.
Berjon calls into question the institutions and infrastructures of the web, suggesting the need for explicitly capture-resistant designs. These can be brought about through technical shifts like new security standards as well as through regulatory practices like antitrust laws. Above all he suggests that these infrastructures must be “subject to either exit or voice (or both).” That is to say that users need to be co-governors in the systems they interact with and need to be able to leave those systems for better alternatives when they no longer serve them.

We can see from this how even anti-institutional projects, like many within the blockchain movement, are subject to capture. For instance, PoW and PoS systems open up opportunities for capture by a minority of miners or stakers. Because a large amount of capital is needed to have real influence and make participation profitable, the governance of these systems can quickly become exclusionary. Here what is captured might not be what gets written to the ledger, but the ledger itself, and thus all the associated rents such as gas fees which are set by these parties and which control who has access to the infrastructure are also captured.
...users need to be co-governors in the systems they interact with and need to be able to leave those systems for better alternatives when they no longer serve them.
Uncapturable (or Unenclosable)
Anticapture is an organizational response to capture, and Capture Resistance aims to open conversation between regulators and software architects, adding to this we now introduce an architectural response to capture at a foundational layer of communication.
After all, capture can also happen through the manipulation of the medium of communication itself. This overlaps heavily with Berjon’s concerns as we’ll see, but is also a vulnerability for the Anticapture framework. If you can’t trust the system you are communicating over, then you can’t trust the decisions you make as an organization.
In order to make an uncapturable form of writing, we developed Holochain as an open source, data integrity engine for building peer-to-peer apps.
We term any communications medium that avoids capture by its very nature an uncapturable carrier. For instance, the air through which sound travels is uncapturable (so long as no one invents a cone of silence). Conversely, messages sent by intermediary or through writing can be contorted, lost, or otherwise captured in transit, opening up vulnerabilities in the system. Scaling communication through the air is vastly limited; you can only speak so loudly. So creating a form of scalable communication that is uncapturable is key to addressing the forms of capture introduced by large scale systems and societies. In order to make an uncapturable form of writing, we developed Holochain as an open source, data integrity engine for building peer-to-peer apps. The technical details for how Holochain secures the communication architecture will be described for a general audience in forthcoming materials, but in the meantime we refer you to an alpha draft of our whitepaper. It is also worth noting that our implementation doesn’t require any centralized servers or a shared global ledger and thus avoids the forms of capture that those systems open up, either in governance and security or in regulation.
Capture here is about more than just the security of communications. Holochain also ensures that users always possess their own data and can take it into new spaces they create or join. This combats the capture of privatization.
We previously termed this architectural intervention an “unenclosable carrier” in reference to the enclosure of the commons, a term originally referring to the privatization of public land which the commoners of England relied on. However, it can also be used to refer to any privatization of public resources, from literal enclosure with fences to the paywalling of publicly funded research or the patenting of plant genomes. More generally enclosure is a form of capture and so we have shifted our terminology to speak about Holochain as an uncapturable carrier in order to recognize how it serves as a base layer architecture that can support a broader capture-resistant framework.
Holochain and Capture Resistance
The introduction of an uncapturable carrier provides several tools that can help address the four security threats that Berjon describes. Along with several other intrinsic privacy benefits, Holochain’s peer-to-peer data structures break cloud services’ monopoly on data and privacy. This brings its own set of challenges, for instance Holochain’s accountability mechanisms force certain data into the public sphere; but unlike blockchains with their global visibility, the required data transparency only extends to the group level. Similarly, defaults and intermediation are at least in part solved by easy forking of both platform and data in what we call walkaway. And opaque mechanism design is limited by shared, openly accessible, consented-to rulesets that can be audited by anyone who can read source code. Without offering one totalizing solution, these tools work together to create capture resistant ecosystems from the ground up. No organization building on Holochain can capture the market or underlying infrastructure because we make exit easy and thus provide users the opportunity to build-in voice.
No organization building on Holochain can capture the market or underlying infrastructure because we make exit easy and thus provide users the opportunity to build-in voice.
Holochain and Anticapture
This brings us back to governance as users need to be able to govern their shared platforms, communities, and resources. Holochain and uncapturable carriers can help support the Anticapture framework in a number of ways. For one, because anyone can host the software and act directly peer-to-peer without a central server or ledger, the community gains a high level of autonomy. Beyond that, having clear, mutually shared rulesets helps to maintain security and ensure clarity through the varied governance stages. Holochain also follows almost the same process as laid out by Anticapture for changing the internal ruleset of a community, with the execute stage being managed by each agent for themselves autonomously from the rest. Finally, because every action within a Holochain app is signed, it is easy to trace any form of capture that does happen, no matter the stage of governance. This means communities can address any exploits that arise and continually become more capture-resistant. We explored several of these concepts further in a recent article if you are interested in learning more.
Conclusion
While there are several definitions and arenas of capture presented above, they all share a concern for the ways small, powerful groups can take control of a resource that should be held in common by the larger group, community, or society.
There is a tendency to avoid capture in one area by shifting power to someone or something that is tasked with protecting against that capture. However, that opens up a new opportunity for capture by centralizing power in a new place. Thus we need capture-resistant design across all layers, starting with a strong foundation in the medium of communication.
There is a lot of work still to be done in capture-resistance. We hope this broad overview of capture and capture-resistance frameworks helps you to think through these issues from multiple angles, holding them all in mind to see where they differ, conflict, and benefit each other.
Subscribe to be the first to read our upcoming blog on the power of Walkaway.


